Threats to information security are active across all industries, and hedge funds, which hold sensitive financial data pertaining to their owners and investors, are an especially tempting target.
Security experts note the complexity of operations and legal functions that comprise a fund’s business activities, and the necessity for a comprehensive review of appropriate policies, procedures and training, as well as the technological aspects of preparation.
“On a daily basis we are talking with our clients about cybersecurity-protection of data, protection of the network, security awareness,” said Daniel Bartucci, director of sales and business development at Richard Fleischman and Associates. “It is almost best to operate with the mindset that it is no longer if a security breach will happen, it is what you will do when one happens. Hedge funds are experiencing a surge of infiltrations, whether it’s a phishing e-mail or an encryption virus.”
The questions of responsibility for protecting sensitive information often don’t get asked until it’s too late. Such appears to be the case in the security breach involving the Target retail store chain. Trustwave, Target’s information security provider, was recently named as a defendant in lawsuits relating to the data security breach that affected Target stores in late 2013.
“Contrary to the misstated allegations in the plaintiffs’ complaints, Target did not outsource its data security or IT obligations to Trustwave. Trustwave did not monitor Target’s network, nor did Trustwave process cardholder data for Target,” said TrustWave CEO Robert McCullen in a letter posted to the company’s website on March 29.

Doug Steelman, Dell SecureWorks
Whether it’s hacktivists like Anonymous, criminal actors bent on financial gain, or rogue nation-states, the fundamentals of executing defense from a cyber-perspective are the same across industries, yet the financial industry is a conspicuous target in its own right.
“As with basketball, you can play a zone defense or man-to-man coverage,” said Doug Steelman, chief information security officer at Dell SecureWorks. “The techniques, tactics and procedures of threat actors are consistent across verticals, but the financial sector will have more of a leaning toward criminal threat actors. We still see a lot of commodity threats, but more often we see threats developed specifically for a target.”
The financial vertical is one of Dell SecureWorks largest vertical markets. “We currently protect the informational assets of 1,172 banking and financial organizations including numerous hedge funds,” Steelman said.
CryptoLocker, one of a group of malware known as ransomware, burst on the scene in 2013, aggressively encrypting files on the victim’s system and returning control of the files to the victim only after a ransom is paid.
Early versions of CryptoLocker were distributed through spam emails targeting business professionals (as opposed to home Internet users). The lure was often a “consumer complaint” against the email recipient or their organization. Attached to these emails was a ZIP archive with a random alphabetical filename containing 13 to 17 characters.
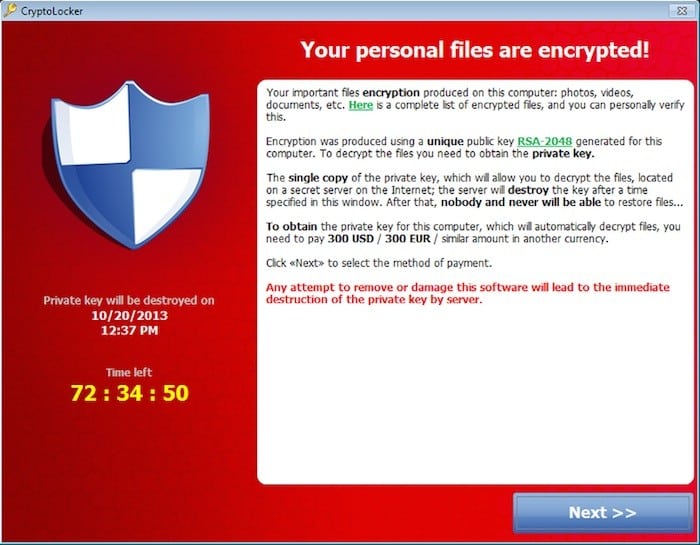
Cryptolocker’s countdown timer. Source: Wikimedia Commons
Ransomware prevents victims from using their computer normally (e.g., by locking the screen) and uses social engineering to convince victims that failing to follow the malware authors’ instructions will lead to real-world consequences.
“Social engineering is still an initial vector for most threat actors,” said Steelman. “Making sure folks are aware from a social engineering perspective is important. It comes back to proper instrumentation. You need to make sure you can see data infiltration.”
That leaves a lot of responsibility upon the end users in the firm. Aside from implementing security tools and technology, promoting security awareness and having a security response plan are all important aspects for every firm, as is extending those practices to your service providers who may require access to your environment.”
“You need to continually have an understanding of your data, understanding who has access to it, and what files are shared,” said Bartucci, noting that last year less than half of all security breaches occurred by “hackers.”
In addition to financial gains, hacking and security breaches can even have a direct impact to the markets. “If you look back to April 23rd last year, the Associated Press’ twitter feed was hacked,” said Bartucci. “As soon as the feed was compromised it posted a bogus story about the White House on fire and the President being injured. It took the Dow down over 100 points. It’s that kind of impact that those behind these breaches look to achieve.”
Featured image via iStock